Microsoft Entra ID (Azure AD)
TL;DR
To integrate Microsoft Azure Active Directory with Query:
- Setup the required connection parameters in Microsoft Graph API mentioned in the 'Prerequisites' section of this document.
- Add a Microsoft Azure Active Directory connection source in Query with the connection parameters
- Test the integration with Test connection link.
- Perform searches for users, devices and authentication events.
Overview
Microsoft Entra ID (Azure AD) is a cloud-based identity and access management service provided by Microsoft, offering secure authentication and authorization capabilities for applications and resources in the Azure and M365 ecosystems.
By integrating your Entra ID tenants with Query, you can search for Users, Groups, Devices (Machines) stored within the directory as well as sign-in (Authentication) logs for each user as well as email delivery activity.
Prerequisites
This connector DOES NOT WORK for Entra ID Free Tier. You must have an Entra ID Premium P1 or Entra ID Premium P2 license, or another license which includes that product, such as Microsoft M365 E5.
Create an App Registration
You must do the following steps to use the APIs and create the connection credentials. You can access Azure AD API with Application Context or User Context. Query will use the Application Context (Link) to access the API. For more information about creating an Enterprise Application see here
Add Microsoft Graph API permissions
The following Application Permissions are necessary for Query to search Microsoft Entra ID (Azure AD) to retrieve users, their devices, group information, and authentication events as shown below (FIG. 1). Ensure you provide Admin Consent after adding the permissions.
ThreatHunting.Read.AllAuditLog.Read.AllDevice.Read.AllDirectory.Read.AllDomain.Read.AllGroup.Read.AllUser.Read.All
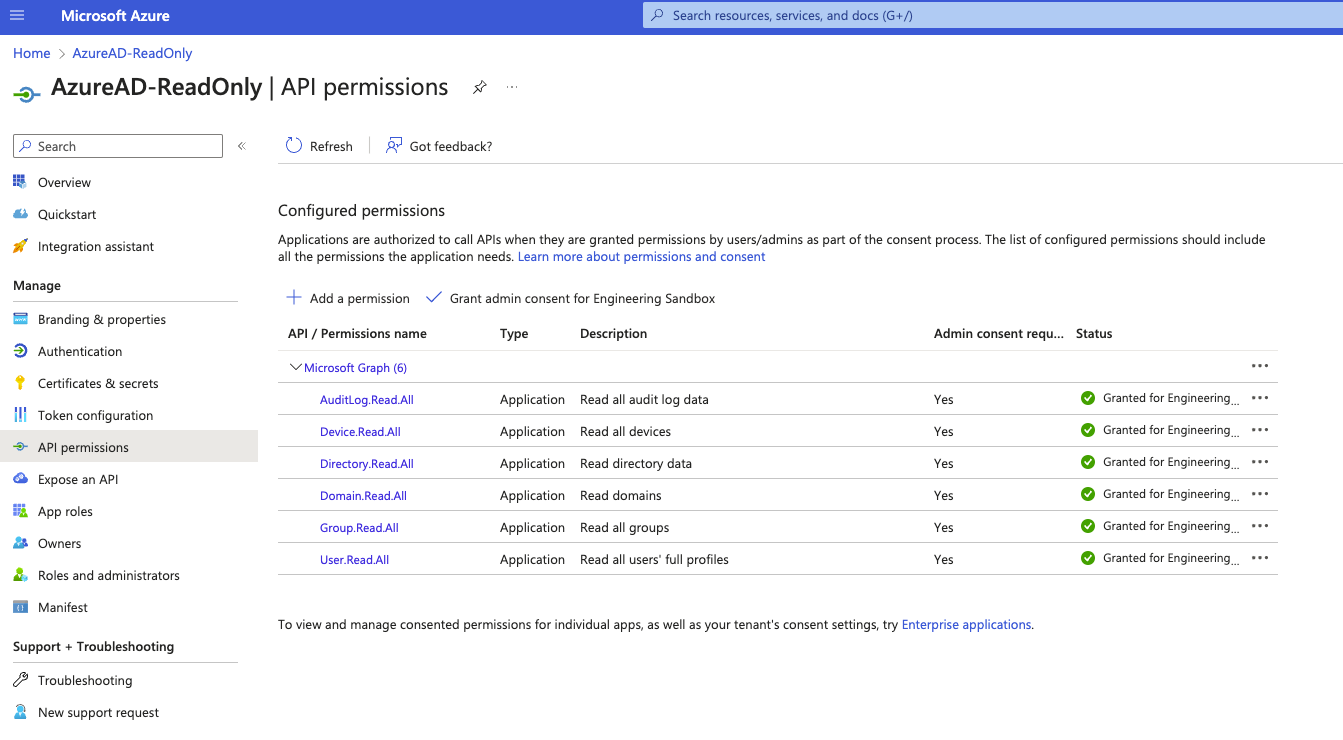
FIG. 1 - API Permissions required for Microsoft Entra ID connector Application Registration
Generate Client Secret credential
To generate a Client Secret for the Application Registration see here. Set an expiration value between 6 months and 2 years and copy the Secret Value, NOT THE SECRET ID!
Return to the Overview section to also retrieve the value of the Client (App) ID and the Tenant (Directory ID).
Configure a Microsoft Entra ID Connector
-
Navigate to the Connections page, select Add Connections, and select Microsoft Entra ID (Azure AD) from the Identity and HR category, optionally type "Entra ID" in the search bar as shown below (FIG. 2).
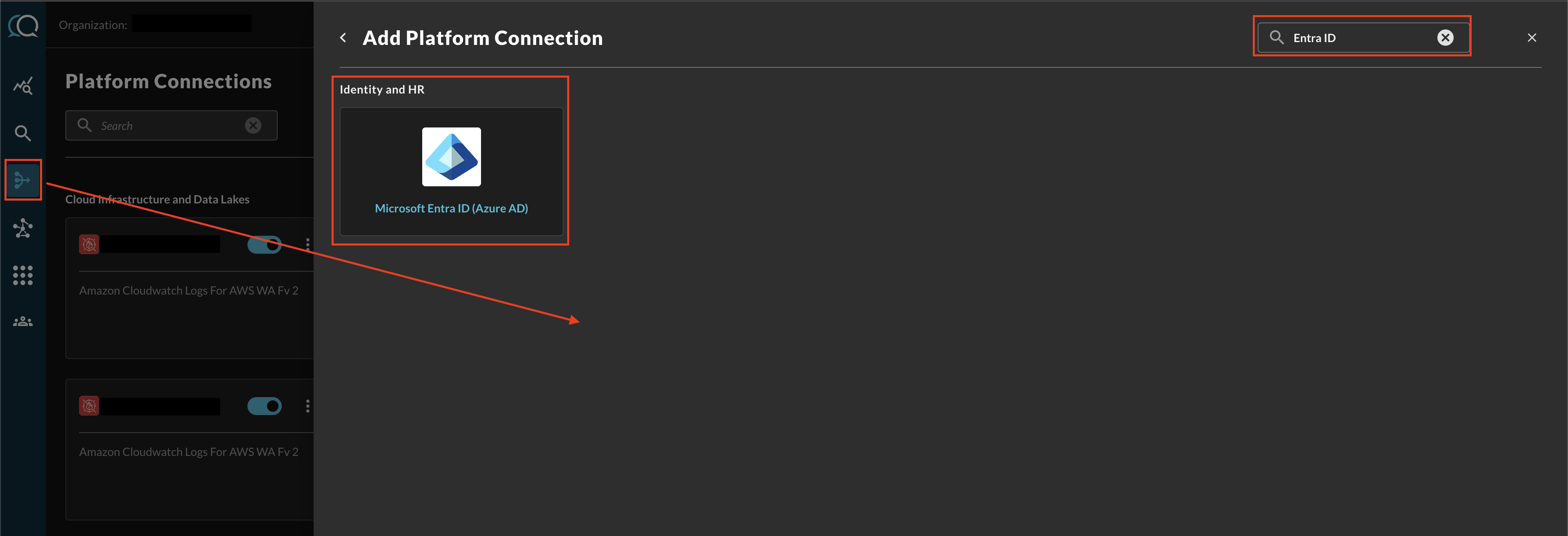
FIG. 2 - Locating the Microsoft Entra ID (Azure AD) Platform Connector
-
In the Connection Info section of the platform connector, provide the following details, select Save, and then Test Connection as shown below (FIG. 3).
-
Connection Alias Name: A contextual name for the Connector, this is used to disambiguate multiple of the same connector.
-
Microsoft Entra ID Tenant ID: The Tenant (Directory) Identifier of your Entra ID tenant.
-
Microsoft Entra ID Client ID: The Client (Application) Identifier of the Enterprise Application you created.
-
Microsoft Entra ID Client Secret: The Value of the Client Secret you generated for the Enterprise Application you created.
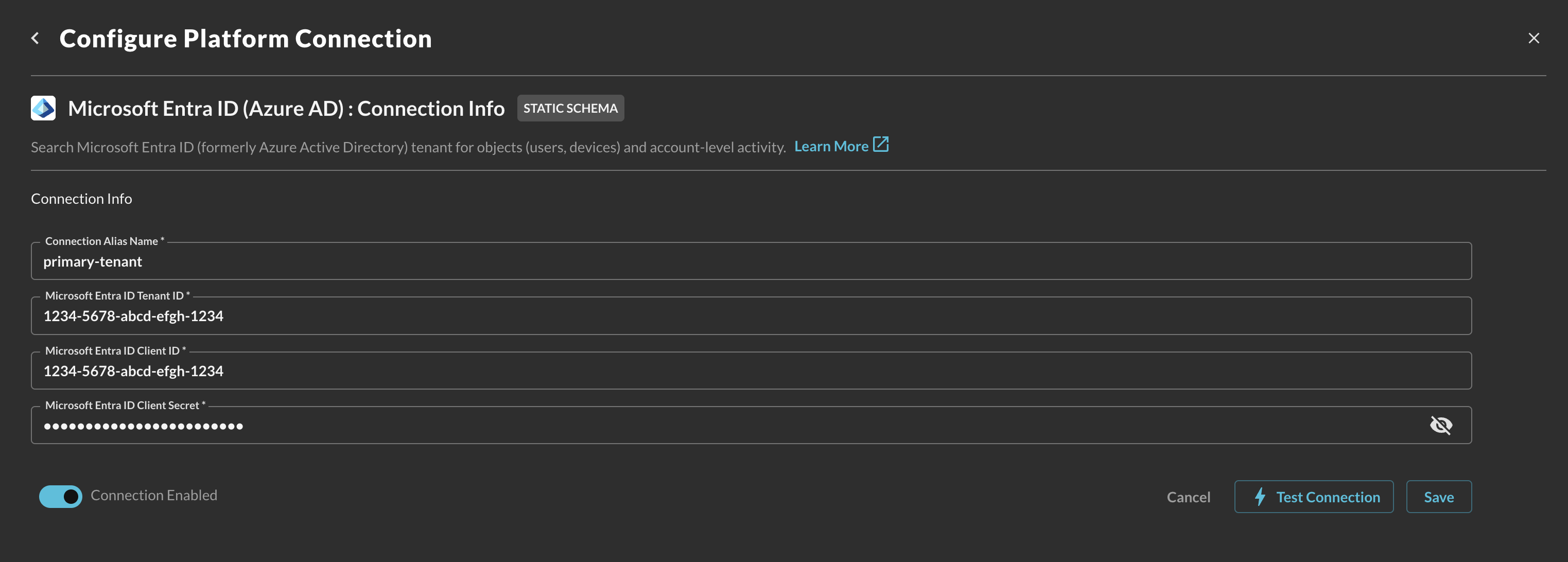
FIG. 3 - Configuring the Connector
-
After you have verified you can successfully test the connection, you are ready to perform Federated searches against your Microsoft Entra ID tenant!
Querying the Microsoft Entra ID (Azure AD) Connector
Within the Query Search UI, all Platforms (A.K.A Connectors) are enabled by default, to check that Microsoft Entra ID (Azure AD) is enabled, navigate to the Identity & HR section of the Platforms dropdown and ensure that Microsoft Entra ID (Azure AD) is selected (denoted by a checkbox) before running your searches as shown below (FIG. 4).
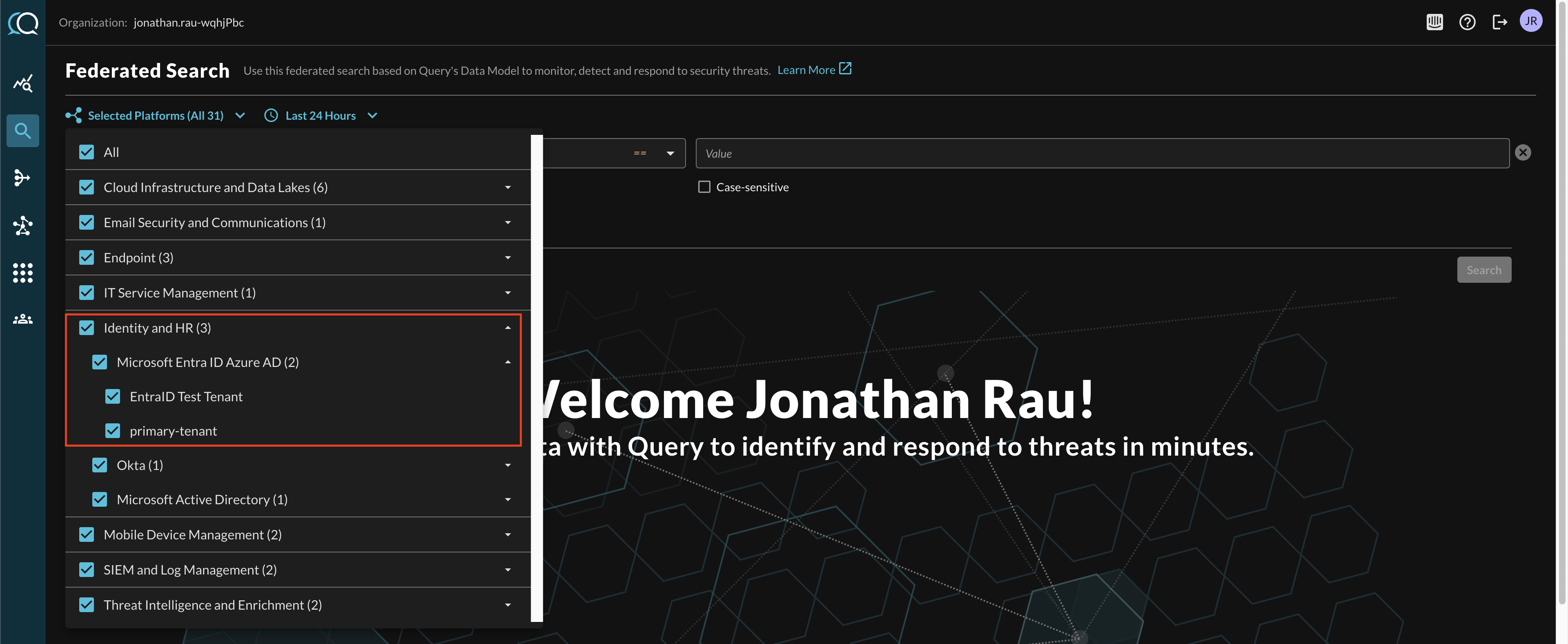
FIG. 4 - Ensure Platform Connectors are selected for search
If you configured multiple Connectors their actual Platform Connection Name will appear in another sub-section.
The following Entities, Events and Objects are supported by Query for those data points. For more information about this terminology, refer to the Normalization and the Query Data Model (QDM) section of the docs or check out our QDM Schema website.
Entities
- IP Address - maps to Email
SenderIPv4,SenderIPv6, and Originated From - Email Address - for the Users as well as email and authentication logs
- User Name - the UPN of Users as well as within email and authentication logs
- Resource ID - for assigned devices (
id)
Events
- Email Delivery Activity (legacy)
- Email Activity
- Authentication
Objects
emailosurlusergroupdevicehardware_info
Resources
- Working with Azure Active Directory resources in Graph API
Updated 9 days ago